An Introduction to Cybersecurity
On November 2, 1988, the Morris worm became one of the first large-scale attacks on the then-nascent Internet. Robert Morris, a Cornell student, had intended to write a program to measure the size of the Internet — but thanks to a bug, his program ended up shutting down thousands of computer systems.
Although the havoc wreaked by the Morris worm was undeniable, it pales in comparison to the cost of similar attacks today. In the late 1980s, there were less than 100,000 computers connected to the Internet, and those were primarily by scientists and select branches of government. Now, the Internet is a ubiquitous part of our everyday lives, and we rely on it for communication, commerce, healthcare, and more.
In the past, our approach to cybersecurity has been largely reactive — we’ve found and patched leaks only after they’ve been exploited. But as more of the world moves online, we’ll need to take a proactive approach.
The state of cybersecurity in 2020
More than half of the global population now has Internet access, and Cisco projects that that number will rise to two-thirds by 2023. We’re also storing more personal data online than ever before, passing more data and control to Internet-enabled smart devices, and building increasingly complex cloud-based applications that rely on funneling data through a web of integrated systems that may have varying security standards. All of this adds up to a dramatic increase in our vulnerability to data breaches and hacks.
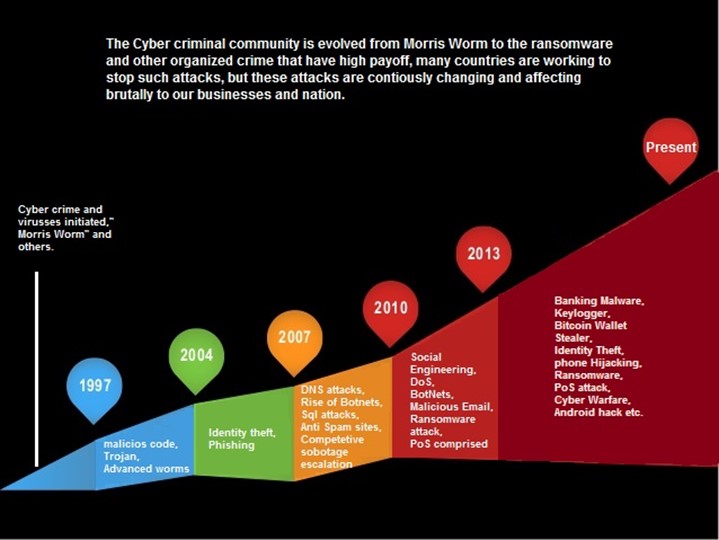
As the two charts below demonstrate, cyber crimes have been increasing rapidly in number and severity over the past three decades; financial losses from these attacks are expected to total $6 billion annually by 2021.

Type and frequency of data breaches, 1988-Present. Source: infosecinstitute.com.
Cybercrimes have also become much more nuanced, sophisticated, and diverse since Morris’ 1988 worm. Today’s cyberattacks include:
- Phishing: Emails, texts, and phone messages that offer rewards or incentives for sharing personal information (phishing now accounts for about 90 percent of successful hacks)
- Ransomware: Holding stolen data “hostage”, either by blocking access or threatening to publish sensitive information, until a ransom is paid
- Point of sale (PoS) attacks: Targeting payment processing systems to steal credit or debit card information
- Identity theft: Stealing personal data in order to impersonate the victim when committing fraud or other criminal acts
- SIM swapping: Gaining access to data and accounts by connecting an unauthorized SIM card to the victim’s phone number
- Digital ad fraud: Generating false clicks and impressions on digital ads to drive up to cost of advertising
- “Deepfakes”: AI-generated videos that misrepresent real people or events; the wide availability of photos and videos online makes these fake videos relatively easy to generate, and they are becoming increasingly difficult to detect
- Fraudulent information: Digital publications and communications spreading misinformation; for example, with the current COVID-19 crisis, we are seeing a spike in online promotions for bogus treatments, vaccines, and other medical products

Major data breaches, 2017-Present. Larger circles represent higher victim numbers; darker colors represent more sensitive data. Source: informationisbeautiful.net.
Cybersecurity solutions
With cybersecurity threats on the rise, a number of proactive counter-measures are being put in place by companies and governments around the world. Some of the most prominent solutions include:
- Regulations such as the GDPR and CCPA, which give consumers more control over how their data is used and stored; these laws have forced many companies to rethink their data practices with an emphasis on security and transparency.
- Bug bounties paid by organizations to individuals who detect and report security weaknesses; according to some estimates, bug “bounty hunters” can earn up to $500K per year.
- Artificial intelligence systems designed to detect cybersecurity vulnerabilities, including systems that use natural language processing to identify sensitive information that may be exposed to hackers.
- Homomorphic encryption, which makes it possible to analyze and manipulate encrypted data without decryption.
- Organizational change, including bringing more women and underrepresented minorities into the cybersecurity workforce, such that diverse perspectives, challenges, and ideas are more consistently represented.
Some of these solutions remain controversial — artificial intelligence, for example, can be used by hackers just as readily as by defenders, and homomorphic encryption is extremely computationally expensive — and no single solution will be effective against every type of modern cybercrime. Taken together, however, they represent a positive shift toward proactivity in cybersecurity.
