Passwords, security, and you
With so much of our personal information stored online, and with security breaches frequently in the news, password security is a big concern for Internet users and developers. In this post, I’ll talk a bit about the different ways passwords can be hacked, the concept of entropy in password security, steps you can take to make your websites or accounts more secure, and how we might expect password technology to evolve over the next few years.
Methods of password attack
There are many different approaches to stealing a password. Below, I’ll describe a few of the most common offline methods. Online attacks, in which an attacker attempts to guess a password directly at the login prompt, are less common (thanks to easier detection and login systems that lock after a certain number of incorrect attempts).
Brute force attacks
In a brute force attack, an attacker illicitly downloads a file of passwords, which are almost always hashed or encrypted. The attacker then attempts to break the hash by systematically looping through combinations of letters, numbers, and symbols until a password is matched.
In theory, a brute force attack always works — if the attacker tries every possible combination of allowed characters, they will eventually break the password hash. However, it’s often impossible in practice, because the computation time required to try every combination can stretch into decades or even centuries if the passwords are sufficiently long.
Dictionary attacks
A dictionary attack is a variation on a brute force attack, but instead of guessing random or systematically generated combinations of letters, numbers, and symbols, the attacker loops through a dictionary of complete words and phrases. Unlike a brute force attack, this approach isn’t theoretically guaranteed to work — but given that many people use simple, common passwords (e.g., “password”, “password123”, etc.) it can be much faster and is often effective.
A further variation on the dictionary attack uses a dictionary of hashed passwords (called a “rainbow table”), which reduces the computation time by eliminating the step of hashing each guess before looking for a match. Attackers can purchase rainbow tables for common hash functions from a variety of illicit websites.
Social engineering
Social engineering attacks rely on psychological vulnerabilities (and carelessness) to steal passwords directly. Common social engineering methods include:
- Phishing emails, which masquerade as official communication from a company or from one of the user’s personal contacts
- Phone calls, in which an attacker pretends to be an official representative requesting information
- “Sticky note” methods, in which an attacker in a physical location simply reads a password that a user has written down
Entropy and password strength
Entropy is a measure of the number of bits needed to encode a message; in the context of password security, this determines how vulnerable a password is to a brute-force attack. The higher the entropy, the stronger the password.
The concept of password entropy dates to the mid-twentieth century, and stems from mathematician Claude Shannon’s early work on information theory — among other major contributions to the field, Shannon developed methods for measuring the information content of a message and the efficiency of information transfer through channels like fiber optic cables.
There are two main factors that influence password entropy: the length of the password (L), and the number of allowed characters (N). The following equation is used to determine entropy (H):

From this equation, we can see that one of the best ways to increase a password’s entropy is simply to increase its length. This table, from a 2012 research paper, shows the time to break a password given various assumptions for L and N:

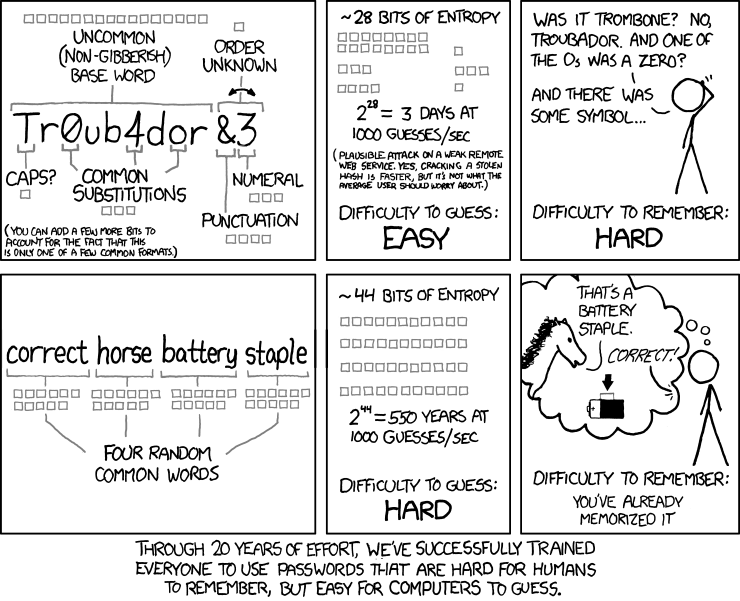
You may also have seen this XKCD comic, which does an excellent job illustrating the advantages of simply choosing a longer password as opposed to a random or complex combination of characters:

How can you make your passwords more secure?
If you develop websites, there are a number of steps you can take to protect your users’ passwords. The simplest of these is to always hash passwords — never store any password as plain text. You can also add a bit of data to each password before applying your hash function; this technique, often called “salting”, can help to prevent rainbow table attacks. Finally, you can hash passwords (especially weaker passwords) twice, a technique known as “key stretching”.
As a website user, you can protect your own passwords by:
- Never reusing passwords. If you do use the same password on multiple sites, you can at least segment your passwords — e.g., use one for social media, one for email, etc. — to reduce risk.
- Using multi-factor authentication on all of your accounts. An authenticator app, physical key (such as a USB dongle), and/or biometric password (such as a thumbprint) can significantly increase security even if your password itself is breached. Note that SMS verification, while still an improvement over a single password, is a more vulnerable authentication method than those listed above.
- Using a password manager (such as 1Password or LastPass) to generate and store unique, strong passwords. Be sure to create a high-entropy master password, and use multi-factor authentication, for your password manager account.
The future of password security
Password security, like most modern technology, is a rapidly-evolving field. There are a few trends that we can expect to influence passwords and their security in the future:
- Multi-factor authentication will become more common, to the point where it’s used on almost all accounts.
- Biometric verification will also become more common, and more reliable. Biometric authentication options might include fingerprint and retina scans, voice and face recognition, and behavioral indicators (e.g., typing or movement patterns).
- Quantum computing will make brute force attacks faster and more feasible — but security providers will also find ways to use quantum computing to improve hashing algorithms and other encryption methods.
