Passwords, security, and you
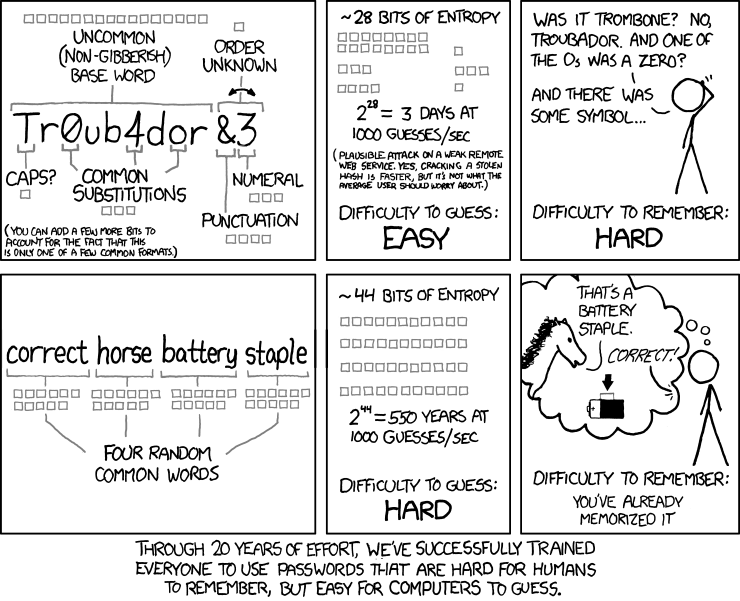
With so much of our personal information stored online, and with security breaches frequently in the news, password security is a big concern for Internet users and developers. In this post, I’ll talk a bit about the different ways passwords can be hacked, the concept of entropy in password security, steps you can take to make your websites or accounts more secure, and how we might expect password technology to evolve over the next few years.